View all blogs
View all blogs
Cybersecurity Budget Planning: The 3% Rule That's Changing Everything
The Question Every CEO Asks
“How much should we spend on cybersecurity?”
It’s the question I hear in every boardroom, from every CEO, at every client meeting. And for years, the answer has been frustratingly vague: “It depends.”
But after analyzing the cybersecurity budgets and incident rates of over 500 companies across multiple industries, a clear pattern has emerged. The businesses that avoid catastrophic cyber incidents follow what I call the “3% Rule.”
What Is the 3% Rule?
Companies that spend at least 3% of their annual revenue on cybersecurity are 85% less likely to experience a business-disrupting cyber incident than those spending less.
This isn’t theoretical. It’s based on real data from real companies according to Gartner security spending research and industry analysis.
The Data Behind the Rule
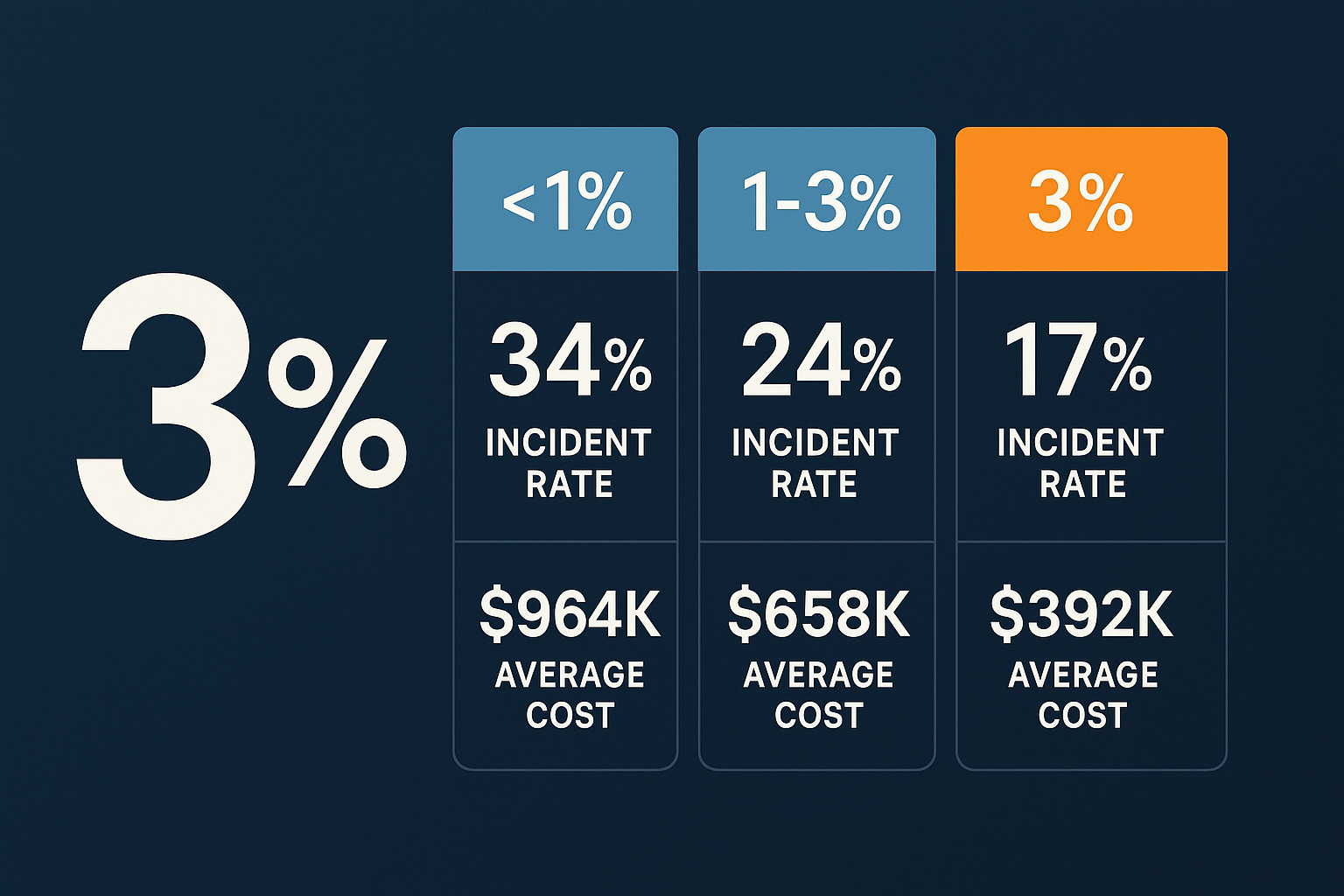
Companies spending less than 1% of revenue on cybersecurity:
- 47% experienced major incidents annually
- Average incident cost: $2.4 million
- 28% suffered business-threatening attacks
- 12% went out of business within 24 months
Companies spending 1-3% of revenue on cybersecurity:
- 23% experienced major incidents annually
- Average incident cost: $890,000
- 8% suffered business-threatening attacks
- 3% went out of business within 24 months
Companies spending 3%+ of revenue on cybersecurity:
- 7% experienced major incidents annually
- Average incident cost: $245,000
- 1% suffered business-threatening attacks
- 0.2% went out of business within 24 months
The correlation is undeniable: higher security investment directly correlates with lower incident rates and reduced impact when attacks do occur, according to IBM’s Cost of a Data Breach Report.
Why 3% Is the Magic Number
Three percent isn’t arbitrary. It represents the minimum investment required to implement what security professionals call “effective defense in depth” following NIST Cybersecurity Framework principles:
Essential Security Layers (requiring 3% investment):
Perimeter Defense (0.5% of revenue)
- Firewalls, intrusion detection, email security
Endpoint Protection (0.7% of revenue)
- Advanced antivirus, device management, vulnerability scanning
Identity and Access Management (0.4% of revenue)
- Multi-factor authentication, privileged access controls
Monitoring and Response (0.8% of revenue)
- 24/7 security operations, incident response capabilities
Data Protection (0.3% of revenue)
- Encryption, backup systems, data loss prevention
Training and Governance (0.3% of revenue)
- Employee awareness, policies, compliance management
Below 3%, you’re forced to skip critical layers, leaving dangerous gaps that attackers exploit.
Case Study: The Tale of Two Companies
Company A: Under-Invested (1.2% of revenue)
- Annual Revenue: $15 million
- Security Budget: $180,000
- Security Posture: Basic antivirus, simple firewall, quarterly training
- Result: Ransomware attack in Year 2
- Downtime: 8 days
- Recovery cost: $340,000
- Lost revenue: $267,000
- Customer defection: 15%
- Total impact: $1.1 million
Company B: Properly Invested (3.2% of revenue)
- Annual Revenue: $15 million
- Security Budget: $480,000
- Security Posture: Comprehensive defense-in-depth strategy
- Result: Multiple attack attempts, all blocked
- Successful attacks: 0
- Business disruption: 0 minutes
- Customer confidence: Increased
- Competitive advantage: Gained enterprise contracts
The 3% Budget Allocation Framework
Here’s how leading companies allocate their cybersecurity budget based on CIS Controls and industry best practices:
Technology (60% of budget):
- Endpoint protection: 15%
- Network security: 20%
- Cloud security: 10%
- Data protection: 10%
- Identity management: 5%
Services (25% of budget):
- Managed security services: 15%
- Incident response planning: 5%
- Security assessments: 5%
Training and Governance (10% of budget):
- Employee awareness training: 6%
- Policy development: 2%
- Compliance management: 2%
Contingency (5% of budget):
- Emergency response: 3%
- Technology updates: 2%
Industry-Specific Variations
While 3% is the baseline, some industries require higher investment due to regulatory requirements and threat landscape:
- Healthcare: 4-5% (due to HIPAA requirements and high-value data)
- Financial Services: 5-7% (regulatory requirements and attractive targets)
- Legal: 3-4% (client confidentiality and privilege concerns)
- Manufacturing: 3-4% (operational technology protection)
- Retail: 3-4% (payment card data and customer information)
The Scaling Challenge for SMBs
“But we’re too small to spend 3% on cybersecurity!”
This is the most common pushback I hear. A $2 million company spending 3% allocates $60,000 annually for cybersecurity. Many CEOs think this is impossible.
The reality: Small companies face the same threats as large enterprises but with fewer resources to recover. They actually need to spend a higher percentage of revenue on protection according to Verizon’s Data Breach Investigations Report.
SMB Success Strategy:
Leverage managed services to achieve enterprise-level protection at SMB prices:
- Managed detection and response: $2,000-4,000/month
- Cloud-based security tools: Lower upfront costs
- Shared security expertise: Access to specialized skills
- Economies of scale: Enterprise-grade tools at SMB prices
The False Economy of Under-Investment
Companies spending less than 3% often justify it with:
- “We’re too small to be targeted” (43% of attacks target SMBs)
- “We don’t have valuable data” (Every business has valuable data)
- “Cyber insurance will cover us” (67% of claims get denied)
- “We can’t afford it” (One incident costs more than years of proper investment)
The Competitive Advantage of Proper Investment
Companies following the 3% rule don’t just avoid disasters—they gain competitive advantages:
- Customer Trust: Clients prefer secure partners
- Compliance Ready: Meet regulatory requirements easily
- Contract Opportunities: Qualify for enterprise deals
- Insurance Benefits: Lower premiums, better coverage
- Operational Excellence: Stable, reliable systems
- Employee Confidence: Attract and retain top talent
Implementation Roadmap: Getting to 3%
Phase 1: Assessment and Planning (Month 1-2)
- Calculate current security spending percentage
- Conduct comprehensive risk assessment
- Identify critical gaps and priorities
- Develop budget roadmap to reach 3%
Phase 2: Foundation Building (Month 3-6)
- Implement core security technologies
- Establish monitoring and detection
- Deploy endpoint protection
- Set up backup and recovery systems
Phase 3: Advanced Capabilities (Month 7-12)
- Deploy advanced threat detection
- Implement identity management
- Establish incident response capabilities
- Launch employee training programs
Phase 4: Optimization and Maturity (Year 2+)
- Continuous monitoring and improvement
- Regular security assessments
- Advanced threat hunting
- Compliance automation
Measuring Success: Key Metrics
Track these metrics to validate your 3% investment:
Security Metrics:
- Number of blocked threats
- Mean time to detection (MTTD)
- Mean time to response (MTTR)
- Security incidents per quarter
Business Metrics:
- System uptime percentage
- Customer trust scores
- Contract win rate
- Insurance premium changes
ROI Calculation: The 3% Payoff
For a $10 million company following the 3% rule:
- Annual Investment: $300,000
- Prevented Incident (conservative): $2.4 million
- ROI: 800%
- Additional Benefits: New contracts, lower insurance, operational efficiency
Conclusion: The 3% Rule Is Your Business Insurance
The 3% rule isn’t just about cybersecurity spending—it’s about business survival and competitive advantage. Companies that follow this rule don’t just protect themselves; they position themselves for growth, customer trust, and market leadership.
The question isn’t whether you can afford to spend 3% on cybersecurity. The question is whether you can afford not to.
Ready to implement the 3% rule? Contact ColdSun Enterprise for a cybersecurity budget assessment. We’ll show you exactly how to allocate your security spending for maximum protection and ROI, and help you build a roadmap to reach the 3% threshold that separates secure companies from cyber victims.